Tackling Foot Pain: Identifying Sources and Implementing Solutions
Foot pain is a pervasive issue, often striking at the heart of daily activities and overall well-being, particularly when it targets the underside of the foot or the arch. Seeking relief becomes paramount, and while consulting a doctor is crucial for diagnosis and treatment, understanding the root causes is equally imperative. From ill-fitting footwear to genetic predispositions, an array of factors can contribute to foot discomfort, necessitating a multifaceted approach to both prevention and remedy. Delving into these diverse origins unveils a roadmap for effective intervention and enhanced foot health.
1. Poor Footwear
Foot pain can have a huge impact on your quality of life. It may prevent you from participating in activities you love or it may keep you awake at night tossing and turning due to your discomfort.
Foot problems like blisters, corns, bunions and hammertoes are often caused by shoes that don’t fit well or provide enough support for your feet. If your shoe size is too small or too big, it puts extra stress on the areas of your feet where you bend and stretch (like the toes and balls of your feet) and over time can cause permanent damage.
Poor footwear can also lead to overuse injuries and conditions such as shin splints, Achilles tendonitis, plantar fasciitis and other issues. Some medical conditions can cause water retention, causing feet to swell and increase in size (causing a poor shoe fit). Pregnancy can also change the shape of your foot (leading to more pressure on specific areas). All of these factors can affect how well your shoes fit and how much support they give your feet.
2. Injury
Your feet are a complex intersection of bones, ligaments, muscles and nerves that work together to allow you to stand and walk. They are also susceptible to injuries that limit their mobility and may require medical treatment from a nearby podiatry clinic.
Injuries can occur due to direct blows or repetitive stress on the foot. This can result in sprains, fractures, metatarsalgia or a broken bone in the ankle. Symptoms of a sprain include pain, tenderness and swelling in the affected area. Muscles and tendons can also be injured if they are overstretched or overloaded. Symptoms of a strain are weakness, difficulty in stabilising the foot, pain working against resistance and bruising.
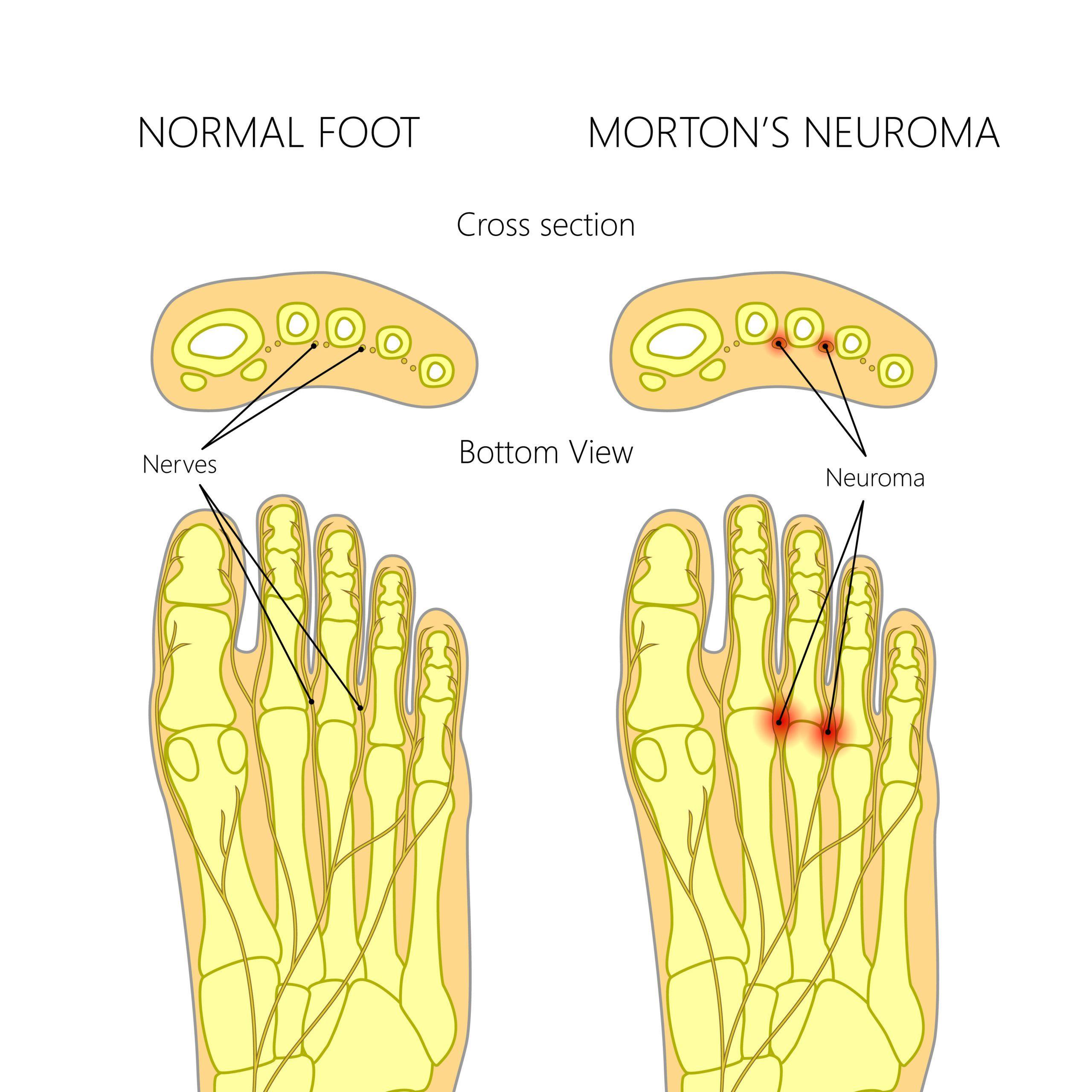
Over time, repeated stress can lead to foot osteoarthritis, a condition that causes the degeneration of cartilage in the joints. This condition usually affects the big toe joint but can also affect other joints in the foot and ankle. Symptoms include pain and stiffness in the joint, which is worse in the morning and improves as the day goes on. Other symptoms include a bump on the base of your toe, or numbness and tingling in your toes (Morton’s neuroma). This condition can be treated with changes in footwear, medications like acetaminophen or non-steroidal anti-inflammatory medication, physical therapy, and ultimately a treatment from the experts at Doubleview Podiatry.
3. Overuse
Many overuse injuries occur in the ball and heel of the foot as a result of excessive pressure or stress. The pain may develop over time or come on suddenly. These injuries include metatarsalgia, sesamoiditis (inflammation of the small bones in the middle of the foot), plantar fasciitis, and shin splints. Those who exercise or play sports frequently are more at risk for this type of injury.
Athletes are especially prone to overuse injury because they often push through the pain to continue their training or playing, especially when they’re competing or practicing for a big event. People whose work demands long periods of standing or walking, as well as those who are overweight, can also suffer from overuse injury.
Overuse injury symptoms can range from mild to severe, and it’s important to seek treatment as soon as you notice them. Resting the injured area, applying ice and taking over-the-counter pain relievers can help speed healing. Seek care from a Wembley Downs podiatrist to avoid the problem getting worse and prevent you from participating in activities you enjoy.
4. Genetics
The 1900s were dubbed the “century of the gene,” as disciplines from comparative anatomy to oncology became infused with genetic concepts and methodologies. Following the completion of the Human Genome Project, genome enthusiasts proclaimed that the major genes for heart disease and mental health disorders would soon be discovered and that genetic cures were on the horizon.
But genetic changes have impacted many aspects of human health, and there’s much more to life than genes (entry: reductionism in biology). For example, the occurrence of the accessory navicular bone has a high heritability, suggesting that it is influenced by genes. The presence of this bone is associated with posterior tibial tendon pathology, flattening of the medial longitudinal arch and foot pain.
But what does this mean for foot conditions like bunions? For one, we can’t blame grandma Rose for her snazzy shoes for giving us bunions – they are caused by pressure from ill-fitting footwear. The same is true for corns, which are a result of repetitive pressure on the skin from footwear. This is why it’s important to choose comfortable, wide shoes and check the fit regularly.
5. Stress
Every person experiences stress differently, but it takes a toll on all parts of the body including the feet. When the feet are stressed, they can become prone to infections such as plantar warts, athlete’s foot or ingrown toenails. Stress can also affect the foot’s internal structures causing them to become painful and inflexible.
The location of the pain is one of the most important clues about what might be causing it. For example, heel pain can be caused by irritation of a thick band of tissue called the plantar fascia that runs across the bottom of your foot from the heel bone to your toes. This is typically felt when you get out of bed or after strenuous exercise like running.
Heel spurs are another common source of foot pain. They are abnormal growths of bone on the bottom of your heel that can develop due to wearing shoes that don’t fit or a misalignment in the way you walk or run. They can be painful and cause you to avoid walking or running for extended periods of time which can cause further injuries.
Addressing foot pain requires a comprehensive understanding of its myriad sources, ranging from footwear choices to genetic predispositions and the impact of stress. By identifying these factors and implementing appropriate solutions, such as proper footwear, seeking timely medical attention for injuries, and managing stress effectively, individuals can embark on a journey toward enhanced foot health and overall well-being. Whether through lifestyle adjustments, medical interventions, or expert guidance from podiatry professionals, taking proactive steps can alleviate discomfort and restore mobility, allowing individuals to pursue their passions with comfort and confidence.
